In this post I wanted to cover how to Activate U2F Fido Keys for AWS root account.
After logging if you click on IAM you will see the dashboard like below where 4 steps are not yet complete. We will complete those first steps and other post will cover the other steps such that we can have better security in our AWS account.
Activate MFA on your root account
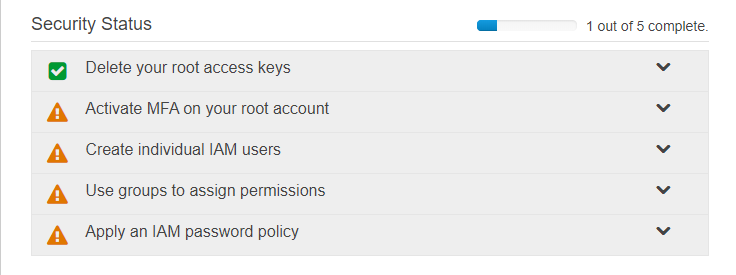
AWS Security Status
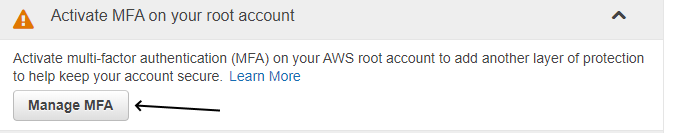
AWS Active MFA
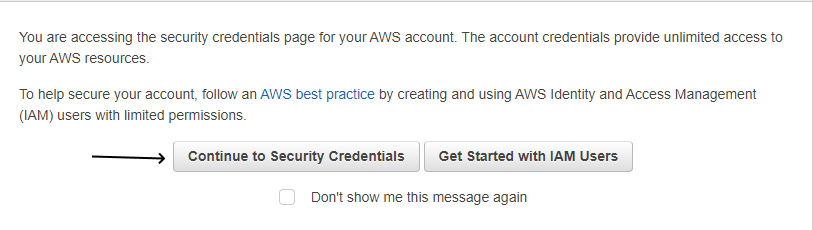
Continue Security Credentials
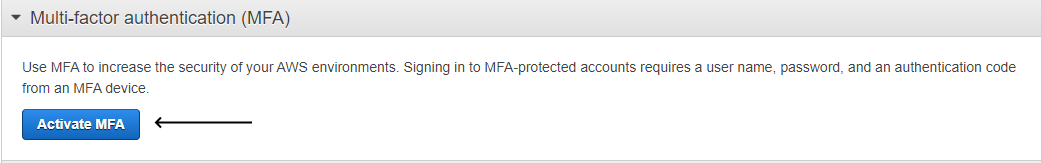
AWS Active MFA IAM Dashboard
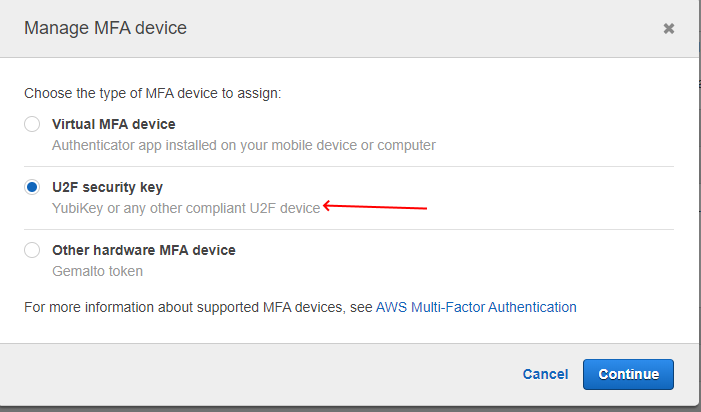
Active MFA U2F

YubiKey
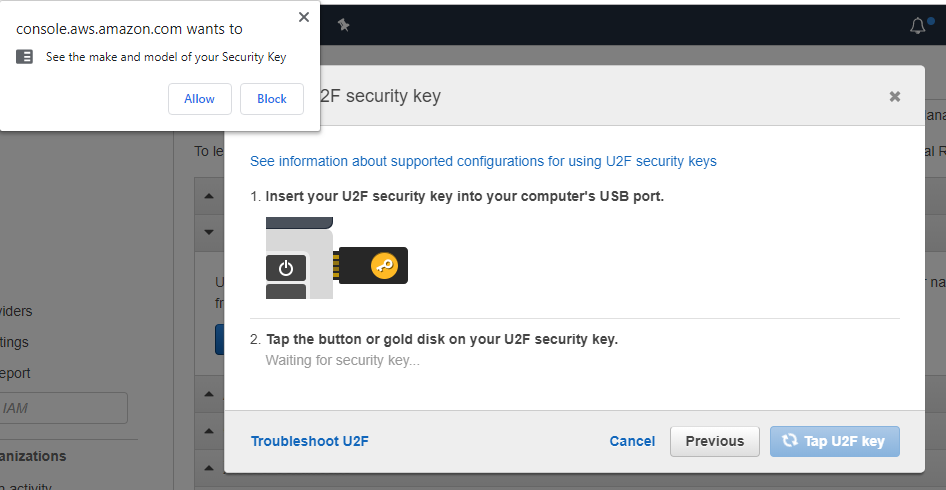
Aws prompt u2f brower allow prompt
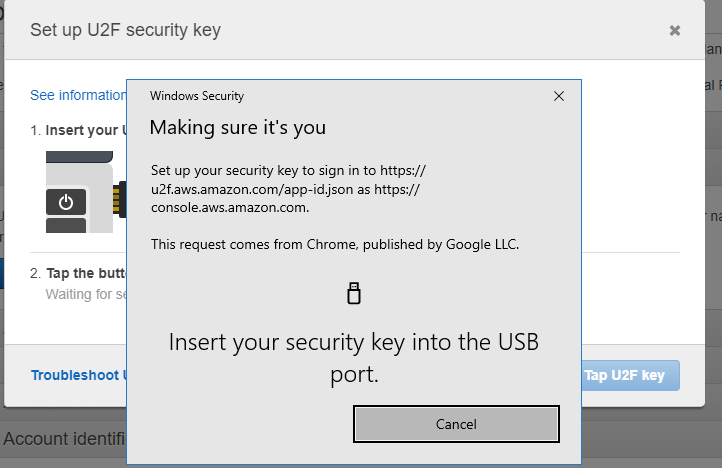
Aws prompt u2f windows prompt
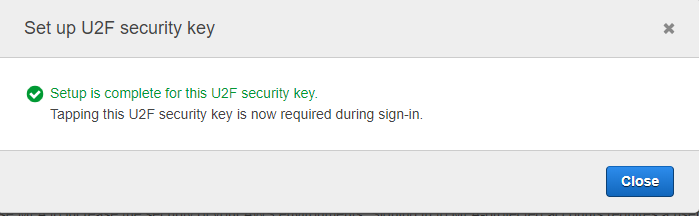
AWS Setup U2F Complete
Summary
I hope this has helped in setting up U2F with your FIDO token to protect the root account, in other post we will cover the other 3 steps.



Leave A Comment